The Ultimate Showdown: Enterprise Browsers vs. Secure Browser Extensions for Enhanced Online Security
Most security tools cannot see what happens inside the browser, yet that is where the majority of work and risk now resides. Security leaders face a critical decision on how to close this gap: they can either deploy a dedicated Enterprise Browser or add an enterprise-grade control layer to the browsers that employees already use and trust. “The Ultimate Battle: Enterprise Browsers vs. Enterprise Browser Extensions” examines this choice across nine operational rounds, including adoption, data protection, BYOD, productivity, management overhead, remote access, Zero Trust alignment, supply-chain security, and future-readiness. Each round utilises practical enterprise scenarios to compare the two models, highlighting their strengths and trade-offs, making it easier to understand their performance at scale.
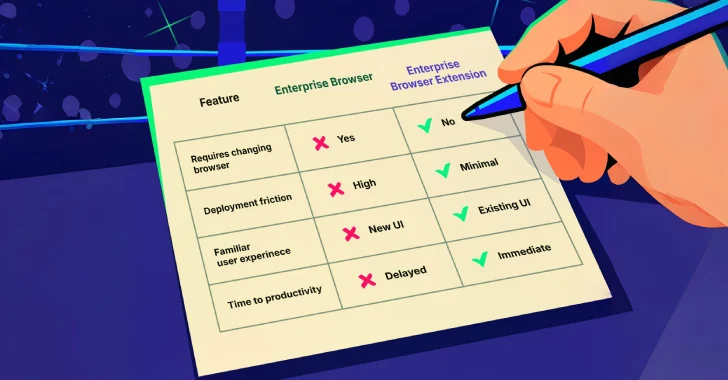
The browser has evolved into the primary workspace for enterprise users, where sensitive data is created, accessed, and transferred through various actions such as copy/paste, form submissions, uploads, downloads, and increasingly, GenAI prompts. Default-browser habits are deeply ingrained, and forcing a switch can hinder adoption, particularly in hybrid environments with unmanaged devices and contractors. While extension ecosystems can enhance functionality, they also increase the potential attack surface. The guide clarifies that neither Enterprise Browsers nor Enterprise Browser Extensions replace the existing security stack; instead, each addresses the in-session security gap differently. The rise of GenAI tools has introduced significant in-session risks, as proprietary information can be pasted into prompts without an audit trail. Controls must effectively distinguish between work and personal accounts in real time, and coverage must extend to unmanaged devices, third parties, and temporary access users. The guide stress-tests both approaches through various scenarios, revealing differences in coverage, control depth, and operational overhead.
Categories: Enterprise Browsers, Browser Security Extensions, Risk Management
Tags: Enterprise Browser, Browser Extensions, Security Tools, Data Protection, BYOD, Zero Trust, GenAI, Risk Management, Adoption, Supply-Chain Security