Protect Yourself from Malicious Facebook Ads: How Meta Verified Can Safeguard Your Account Information
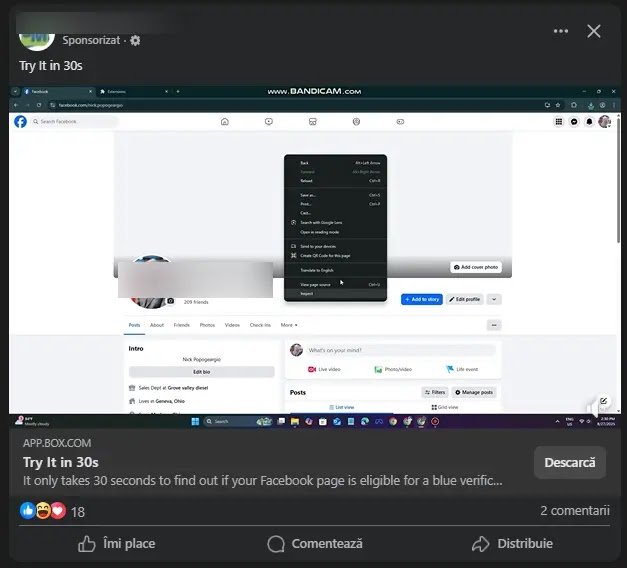
Malicious actors have executed a sophisticated malvertising campaign on Facebook, tricking unsuspecting users into installing a counterfeit “Meta Verified” browser extension. These ads, which appear to be legitimate video tutorials, promise users the coveted blue verification tick without the need to pay Meta’s subscription fee. In reality, the extension is designed to harvest sensitive user data, including session cookies, access tokens, and IP addresses. By utilising trusted platforms like Box.com for hosting, the attackers ensure high availability and evade basic URL-blocking measures, making the scam seem both authentic and risk-free. Analysis by Bitdefender reveals that the video tutorials are linked to Vietnamese-speaking threat actors, with narration and code comments in Vietnamese. Although the extension’s code is clumsily obfuscated and likely generated by an AI-assisted toolkit, it effectively exfiltrates data, including querying the Facebook Graph API to identify high-value corporate profiles.
Victims who follow the tutorial unwittingly grant the extension permissions to read and export cookies from the facebook.com domain. Once installed, the extension immediately activates an exportCookies function that compiles all cookies into a formatted string before sending it to a Telegram bot controlled by the attackers. To enhance the value of the stolen data, the malware queries https://ipinfo.io/json to append geolocation details, increasing its marketability on underground forums. Bitdefender researchers have noted that variants of this extension feature adjustable parameters for tick size and position, indicating an automated pipeline for generating new campaign assets with minimal manual effort. The modular design of the extension also allows for automatic execution upon Chrome startup, ensuring continuous data harvesting even if users disable and re-enable the extension. The core of the infection mechanism lies in the extension’s background script, which hooks into Chrome’s cookies API to extract session tokens without triggering user prompts.
Categories: Malvertising Campaign, Data Harvesting, Browser Extension Exploits
Tags: Malvertising, Facebook, Browser Extension, Data Harvesting, Session Cookies, Access Tokens, IP Addresses, Vietnamese Threat Actors, Geolocation, Infection Mechanism