DOM-Based Clickjacking Vulnerability Poses Risks to Popular Password Managers, Leading to Potential Credential and Data Theft
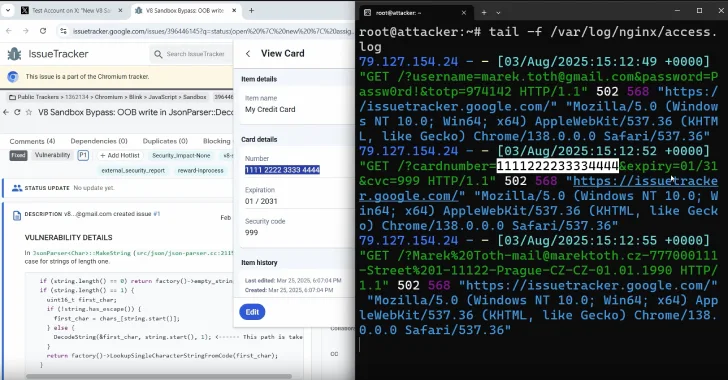
Popular password manager plugins for web browsers have been discovered to be vulnerable to clickjacking security threats, which could potentially be exploited to steal account credentials, two-factor authentication (2FA) codes, and credit card information. This technique, termed Document Object Model (DOM)-based extension clickjacking, was presented by independent security researcher Marek Tóth at the DEF CON 33 security conference. Tóth highlighted that a single click on an attacker-controlled website could enable the theft of sensitive user data, including credit card details and login credentials. The method involves using malicious scripts to manipulate user interface elements injected into the DOM by browser extensions, rendering them invisible and allowing attackers to capture user inputs without their knowledge.
The research specifically examined 11 widely-used password manager browser add-ons, including 1Password and iCloud Passwords, all of which were found to be susceptible to this new clickjacking technique. These extensions collectively serve millions of users. To execute the attack, a malicious actor can create a deceptive website featuring intrusive pop-ups, such as login screens, while embedding an invisible login form. When users attempt to close the pop-up, their credentials may be auto-filled by the password manager and sent to a remote server. Tóth noted that most password managers filled credentials not only for the main domain but also for all subdomains, making it easier for attackers to exploit vulnerabilities. Following responsible disclosure, six vendors have yet to release fixes for the identified vulnerabilities, prompting security experts to recommend that users disable the auto-fill function in their password managers until updates are available.
Categories: Security Vulnerabilities, Clickjacking Attacks, Password Manager Risks
Tags: Clickjacking, Password Managers, Security Vulnerabilities, Two-Factor Authentication, DOM-based, Credential Theft, Auto-fill, XSS, Responsible Disclosure, Fixes