VirusTotal Discovers 44 Undetected SVG Files Utilized for Deploying Base64-Encoded Phishing Pages
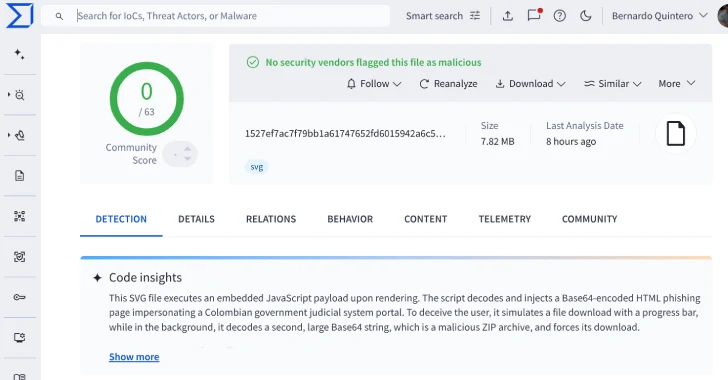
Cybersecurity researchers have identified a new malware campaign that utilises Scalable Vector Graphics (SVG) files in phishing attacks, impersonating the Colombian judicial system. According to VirusTotal, these SVG files are distributed via email and are designed to execute an embedded JavaScript payload. This payload decodes and injects a Base64-encoded HTML phishing page that masquerades as a portal for Fiscalía General de la Nación, the Office of the Attorney General of Colombia. The phishing page simulates an official government document download process with a fake progress bar while stealthily triggering the download of a ZIP archive in the background. The specific contents of the ZIP file remain undisclosed. VirusTotal reported the discovery of 44 unique SVG files, all of which have evaded detection by antivirus engines due to techniques such as obfuscation, polymorphism, and the inclusion of excessive junk code.
In addition to this SVG-based campaign, cracked versions of legitimate software and ClickFix-style tactics are being employed to lure users into infecting their Apple macOS systems with an information stealer known as Atomic macOS Stealer (AMOS). This malware poses significant risks, including credential stuffing, financial theft, and other follow-on attacks. AMOS is designed for extensive data theft, capable of stealing credentials, browser data, cryptocurrency wallets, Telegram chats, VPN profiles, keychain items, Apple Notes, and files from common folders. Trend Micro has noted that AMOS indicates macOS is no longer a peripheral target. As macOS devices become more prevalent in enterprise environments, they have emerged as attractive targets for attackers. The attack chain typically involves targeting users seeking cracked software on sites like haxmac[.]cc, redirecting them to fraudulent download links that trick them into executing malicious commands in the Terminal app, thereby deploying AMOS. Apple’s Gatekeeper protections prevent the installation of .dmg files lacking proper notarisation, requiring application packages to be signed by identified developers and notarised by Apple. With the release of macOS Sequoia, attempts to install malicious or unsigned .dmg files are blocked by default. While this does not entirely eliminate the risk, especially for users who may bypass built-in protections, it raises the barrier for successful infections and compels attackers to adapt their delivery methods.
Categories: Malware Campaigns, Phishing Attacks, macOS Security Threats
Tags: Malware, Phishing, SVG Files, JavaScript, HTML, ZIP Archive, Obfuscation, macOS, Credential Theft, ClickFix