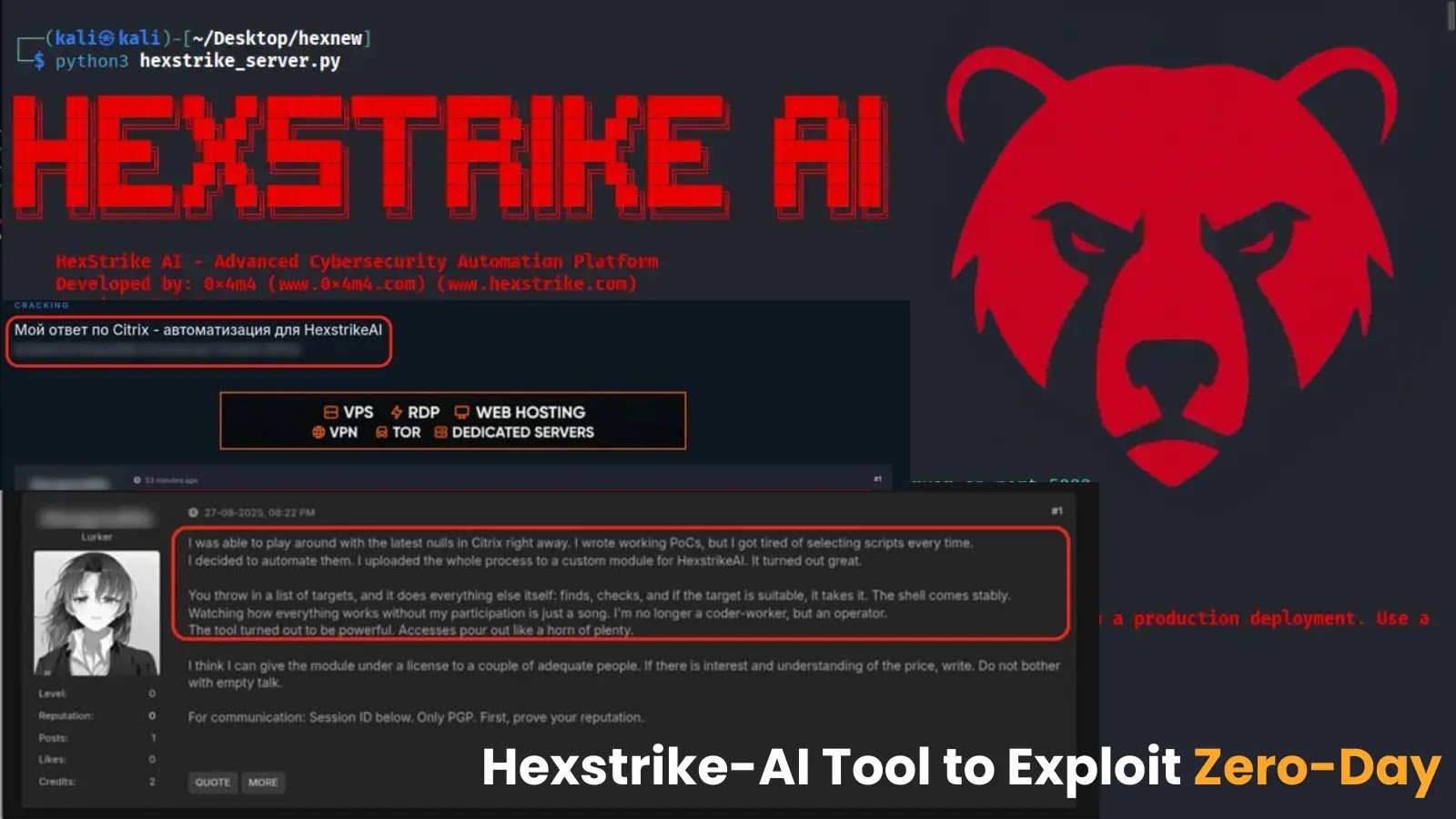
Cybercriminals Utilize Hexstrike-AI Tool to Exploit Zero-Day Vulnerabilities in Just 10 Minutes
Threat actors are swiftly weaponising Hexstrike-AI, a newly released AI-powered offensive security framework, to scan for and exploit zero-day CVEs in under ten minutes. Originally designed for red teams, Hexstrike-AI’s architecture has been repurposed by malicious operators within hours of its public launch. This framework automates zero-day exploits, linking large language models to over 150 security tools for resilient workflows. Recent dark web discussions indicate that threat actors are actively testing Webshell deployments against the newly disclosed Citrix NetScaler ADC and Gateway CVEs, specifically CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424.
Hexstrike-AI operates on a FastMCP server core, enabling AI agents to execute standardised functions without human intervention. The MCP orchestration layer translates high-level commands into sequenced technical workflows, managing each stage of the attack process, from reconnaissance to exfiltration. Check Point’s analysis reveals that operators achieved unauthenticated remote code execution on vulnerable appliances and deployed web shells in under ten minutes. The architecture of Hexstrike-AI includes an abstraction layer that converts vague operator intent into precise function calls, as well as autonomous MCP agents that bridge large language models with various tools. This innovative framework exemplifies the academic projections of AI orchestration driving next-generation cyberattacks, now realised in Hexstrike-AI’s code.
Categories: AI-Powered Cybersecurity, Zero-Day Exploits, Threat Actor Tactics
Tags: Hexstrike-AI, Zero-Day, CVEs, Offensive Security, Automation, LLMs, Exploits, Citrix, Webshell, Cyberattacks