Ukrainian Network FDN3 Initiates Large-Scale Brute-Force Attacks Targeting SSL VPN and RDP Devices
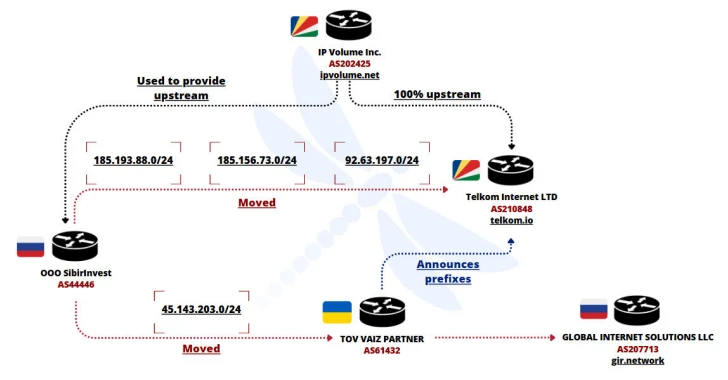
Cybersecurity researchers have identified a Ukrainian IP network, FDN3 (AS211736), as being involved in extensive brute-force and password spraying campaigns targeting SSL VPN and RDP devices during June and July 2025. According to a report from French cybersecurity firm Intrinsec, FDN3 is believed to be part of a larger abusive infrastructure that includes two other Ukrainian networks, VAIZ-AS (AS61432) and ERISHENNYA-ASN (AS210950), along with a Seychelles-based network named TK-NET (AS210848). All these networks were allocated in August 2021 and frequently exchange IPv4 prefixes to evade blocklisting, thereby continuing their malicious activities. AS61432 currently announces a single prefix, 185.156.72[.]0/24, while AS210950 has two prefixes, 45.143.201[.]0/24 and 185.193.89[.]0/24.
The report highlights that the prefixes from AS61432 and AS210950 have been transferred to networks associated with bulletproof hosting services, which are often fronted by shell companies like Global Internet Solutions LLC and IP Volume Inc. Intrinsec’s findings build on previous disclosures regarding the use of these networks for spam distribution, network attacks, and malware command-and-control hosting. Notably, some IPv4 prefixes announced by FDN3 were previously linked to a Russian network, SibirInvest OOO (AS44446), and a U.S.-based bulletproof hosting solution, Virtualine (AS214940 and AS214943). The brute-force and password spraying activities attributed to these prefixes peaked between July 6 and 8, 2025, and are believed to have been employed by various Ransomware-as-a-Service (RaaS) groups, including Black Basta and RansomHub, as initial access vectors to infiltrate corporate networks.
Categories: Cybersecurity Threats, Malicious Infrastructure, Brute-Force Attacks
Tags: Ukrainian, IP Network, Brute-Force, Password Spraying, SSL VPN, RDP Devices, Autonomous System, Cybersecurity, Malware, Ransomware